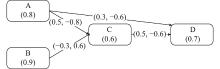
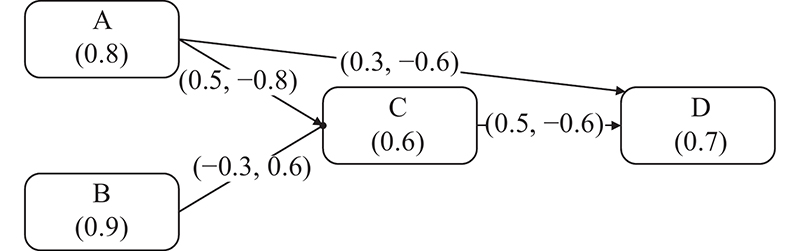
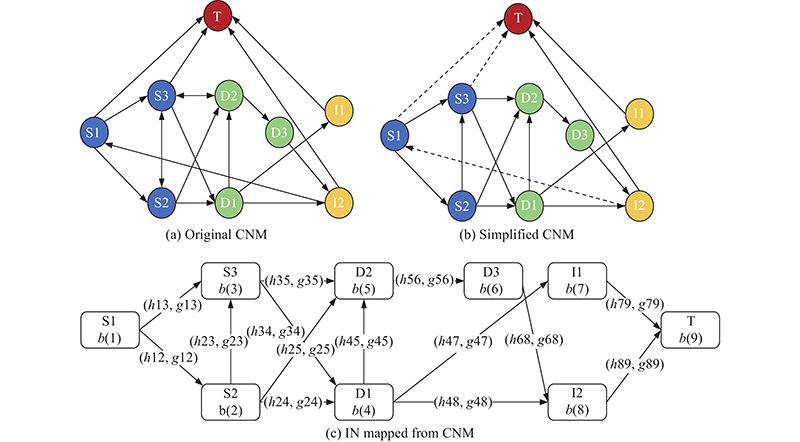
Journal of Systems Engineering and Electronics ›› 2023, Vol. 34 ›› Issue (2): 374-395.doi: 10.23919/JSEE.2023.000019
• • 上一篇
-
收稿日期:2021-03-15出版日期:2023-04-18发布日期:2023-04-18
Network-based structure optimization method of the anti-aircraft system
Qingsong ZHAO1,*( ), Junyi DING2(
), Junyi DING2( ), Jichao LI1(
), Jichao LI1( ), Huachao LI1(
), Huachao LI1( ), Boyuan XIA1
), Boyuan XIA1
- 1 College of Systems Engineering, National University of Defense Technology, Changsha 410073, China
2 International Office of Cooperation and Exchanges, National University of Defense Technology, Changsha 410073, China
-
Received:2021-03-15Online:2023-04-18Published:2023-04-18 -
Contact:Qingsong ZHAO E-mail:zhaoqingsong@nudt.edu.cn;Lexi.ding9512@gmail.com;ljcnudt@hotmail.com;llihuachao_nudt@163.com -
About author:
ZHAO Qingsong was born in 1975. He received his M.S. and Ph.D. degrees from National University of Defense Technology, Changsha, China, in 2002 and 2008, respectively. He is a professor in National University of Defense Technology. He was a visiting scholar with the Department of Technology Policy and Management, Delft University of Technology, Netherlands. His research interests include system integration, defense acquisition and system-of-systems architecture design and optimization, and complex system analysis. E-mail: zhaoqingsong@nudt.edu.cn
DING Junyi was born in 1995. She received her M.S. degree from National University of Defense Technology, Changsha, China, in 2019. She is a program manager at the International Office of Cooperation and Exchanges, National University of Defense Technology. Her research interests include system-of-systems modeling and evaluation, network modeling, and temporal constraint resolving. E-mail: Lexi.ding9512@gmail.com
LI Jichao was born in 1990. He received his Ph.D. degree from National University of Defense Technology, Changsha, China, in 2019. He is an associate professor in National University of Defense Technology. His research interests focus on studying complex systems with a combination of theoretical tool and data analysis, including mathematical modeling of heterogeneous information networks, applying network methodologies to analyze the development of complex system-of-systems, and data-driven studying of the collective behavior of humans. E-mail: ljcnudt@hotmail.com
LI Huachao was born in 1994. He received his B.S. degree from National University of Defense Technology, Changsha, China, in 2022. He is a M.S. candidate in National University of Defense Technology. His research interests include system of systems engineering, complex systems, and systems evaluation and optimization. E-mail: llihuachao_nudt@163.com
XIA Boyua was born in 1994. He received his M.S. degree from National University of Defense Technology, Changsha, China, in 2017. He is a Ph.D. candidate in National University of Defense Technology. His research interests include defense acquisition, complex systems, and system portfolio selection and optimization. E-mail: xiaboyuan@nudt.edu.cn -
Supported by:This work was supported by the National Natural Science Foundation of China (72071206)
引用本文
. [J]. Journal of Systems Engineering and Electronics, 2023, 34(2): 374-395.
Qingsong ZHAO, Junyi DING, Jichao LI, Huachao LI, Boyuan XIA. Network-based structure optimization method of the anti-aircraft system[J]. Journal of Systems Engineering and Electronics, 2023, 34(2): 374-395.
"
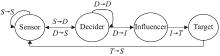
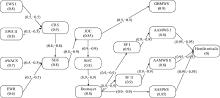
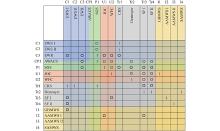
| Network edge | Meaning |
| | A sensor scouts a target and acquires its intelligence |
| | A sensor shares intelligence with another sensor entity |
| | A sensor uploads reconnaissance information to a decider entity |
| | One decider entity receives a control command from a decider entity |
| | One sensor entity receives the control command from a decider entity |
| | An influencer entity receives control command from a decider entity |
| | An influencer entity attacks a tatget |
"
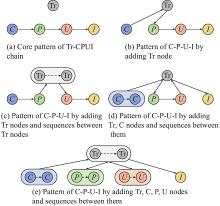
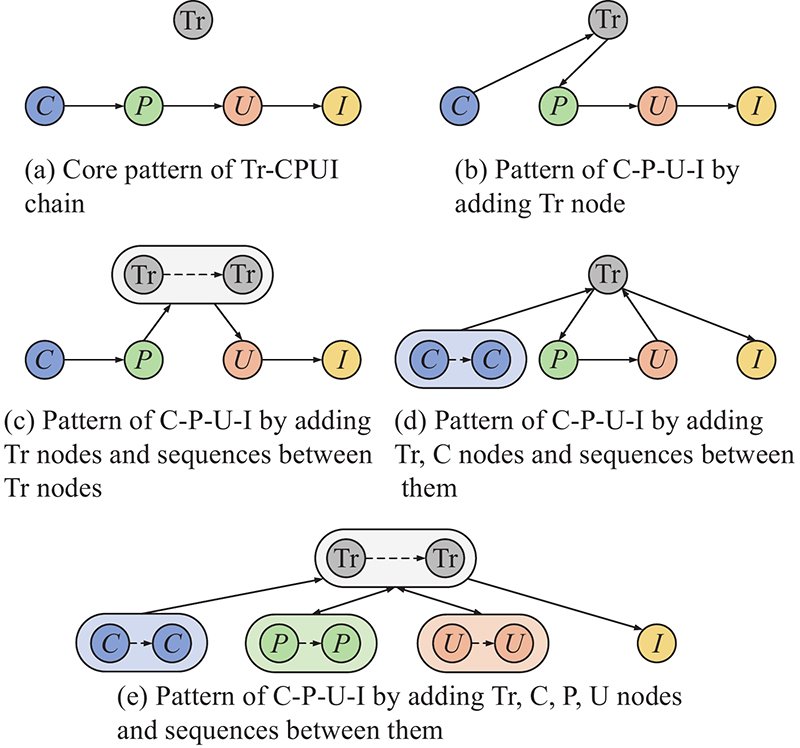
| Attack chain | Meaning |
| | The typical attack chain |
| | The attack chain with sensors’ information sharing |
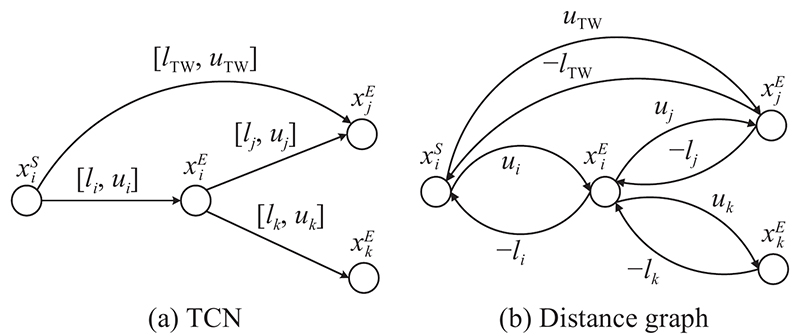
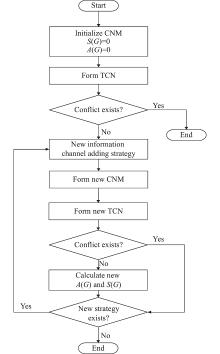
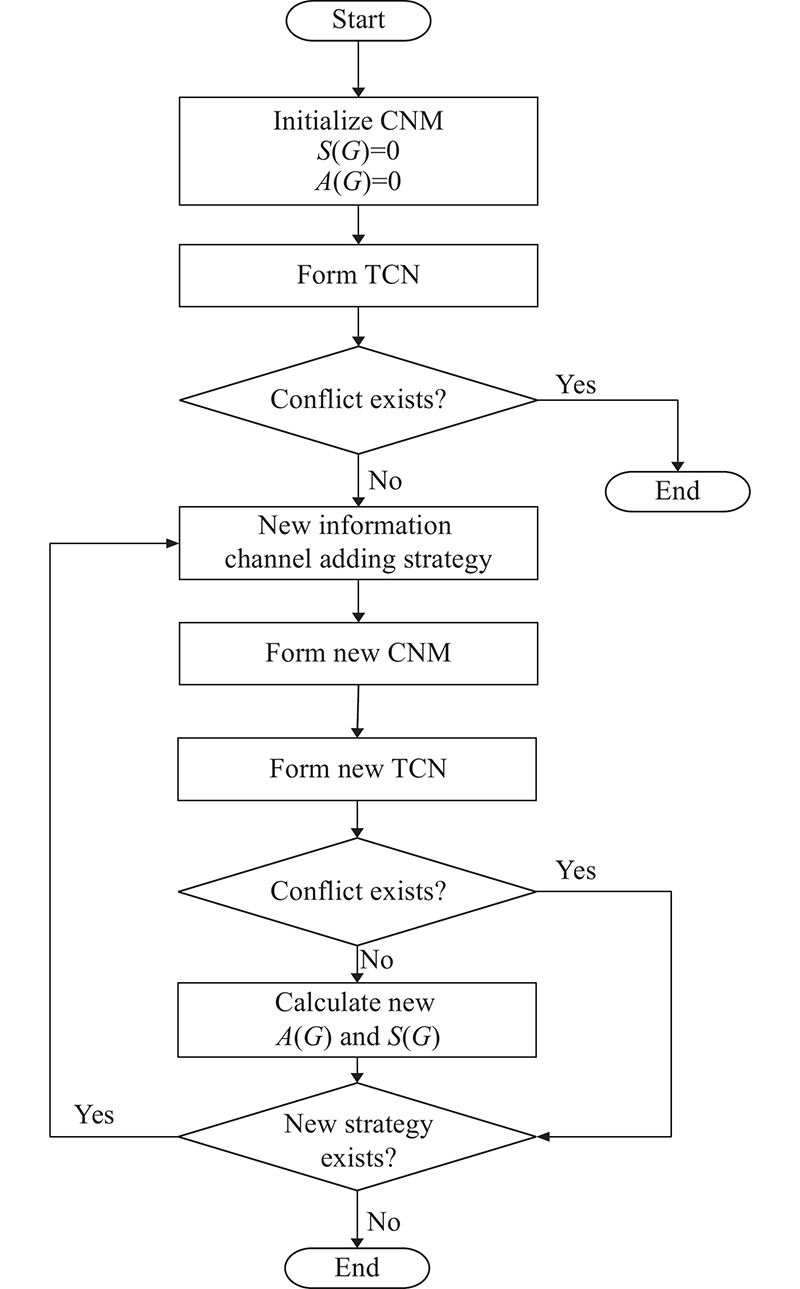
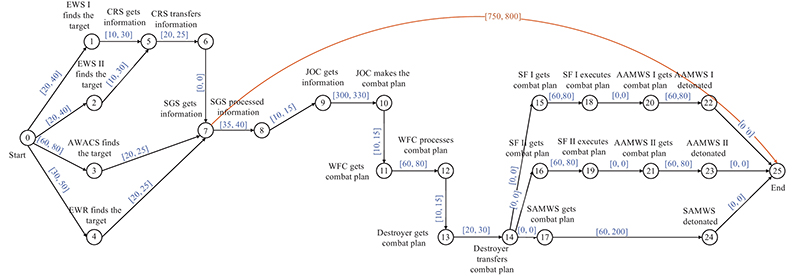
| | The attack chain with deciders’ cooperative command |
| | The attack chain with both information sharing and cooperative command |
| | The attack chain experiencing information feedback |
| | The attack chain with information sharing and experiences information feedback |
| | The attack chain with cooperative command and experiences information feedback |
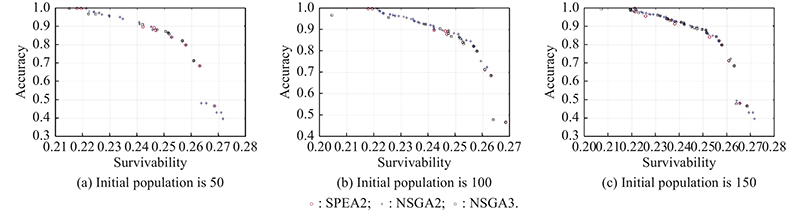
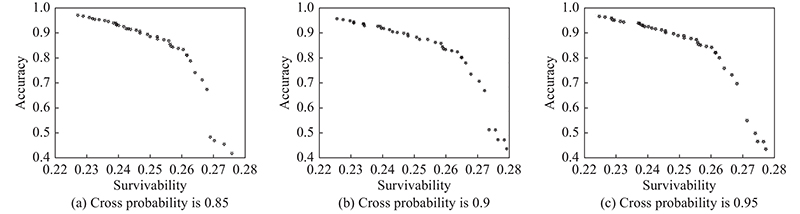
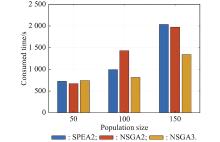
"
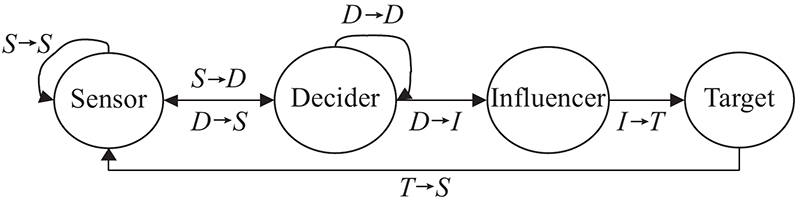
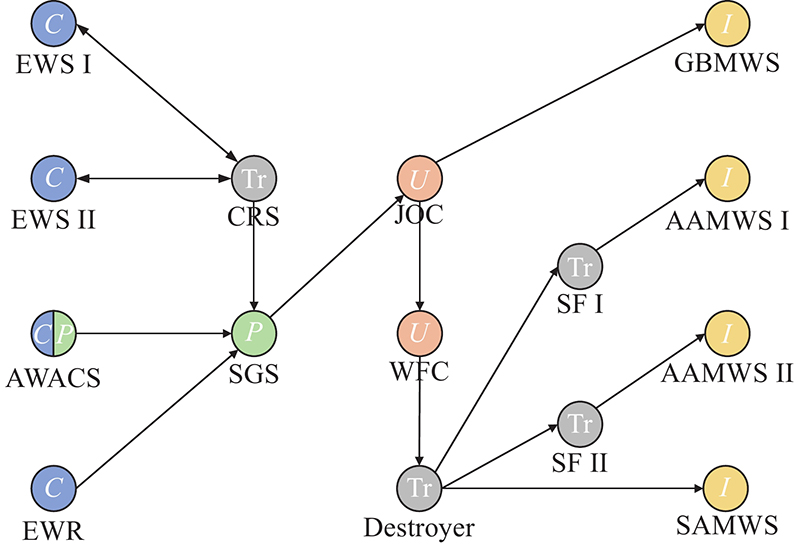
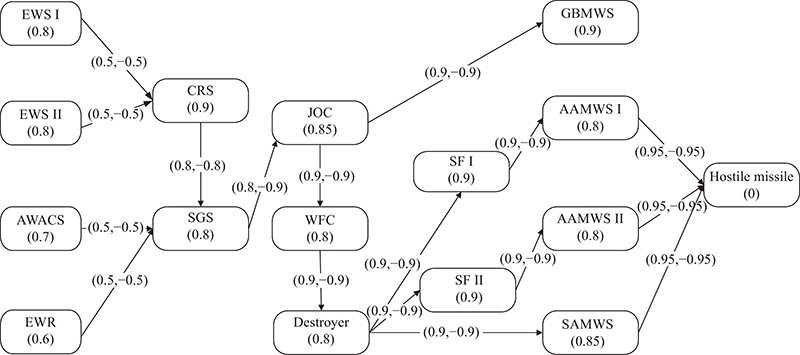
| Node type | Information chain | ||
| Function | Example | ||
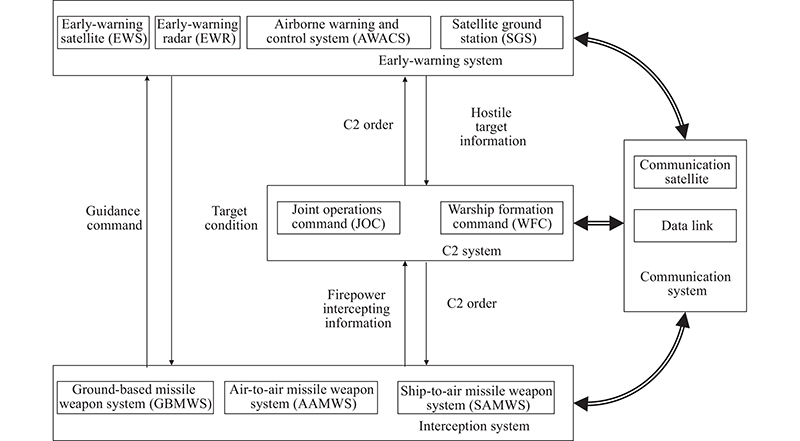
| Sensor ( | Collector ( | Collecting information and detecting targets | EWS |
| Processor ( | Processing information and forming original combat situation | SGS | |
| Transferor ( | Delivering information without amendment and other operation | CRS | |
| Decider ( | User ( | Using information to form a combat plan | JOC |
| Transferor ( | Delivering information without amendment and other operation | Destroyer | |
| Influencer ( | Influencer ( | Destroying targets with firepower | SAMWS |
| Target ( | Ø | Ø | Ø |
"
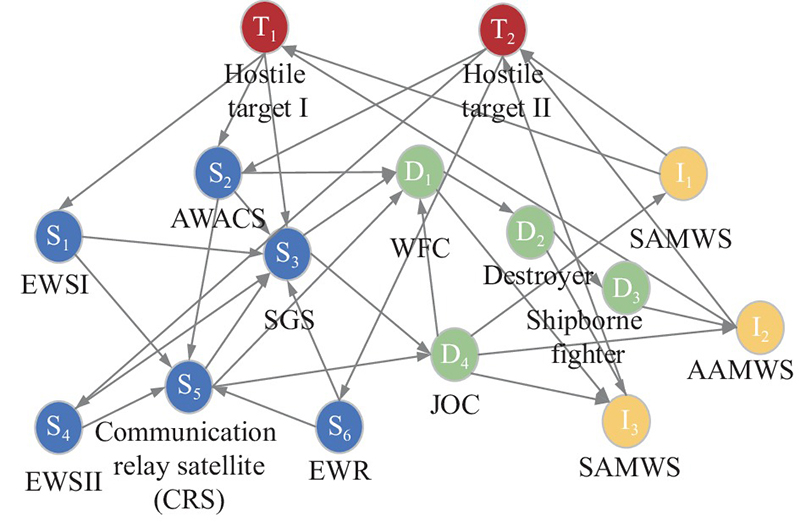
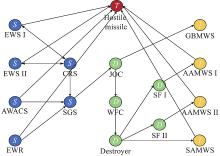
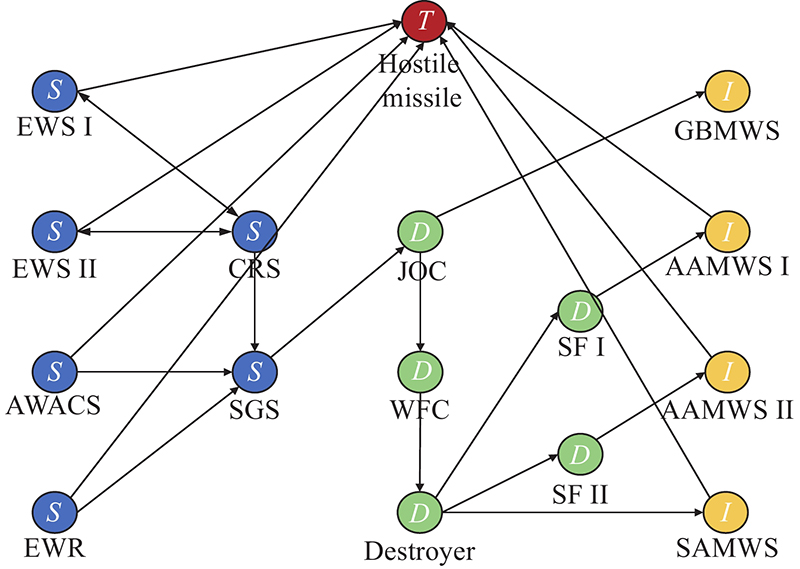
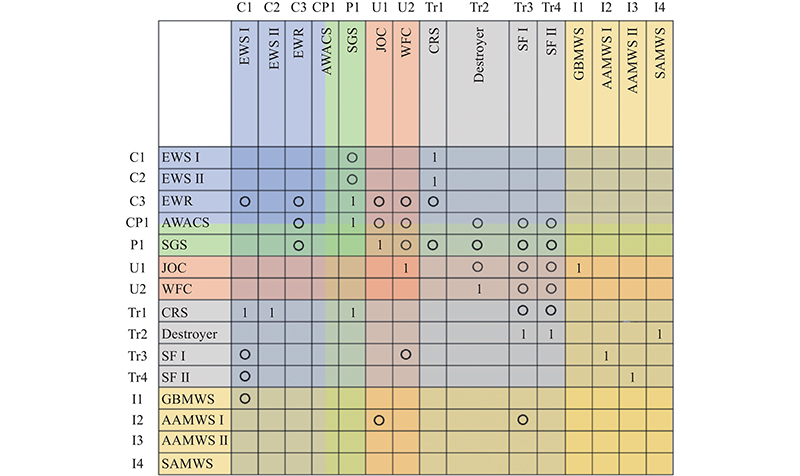
| Type | Combat entity | Combat activity |
| Sensor ( | EWS Ⅰ | Search for target |
| EWS Ⅱ | Search for target | |
| EWR | Search for target | |
| AWACS | Search for target | |
| SGS | Process data | |
| CRS | Transfer data | |
| Decider ( | JOC | Form combat plan |
| WFC | Form combat plan | |
| Destroyer | Transfer command | |
| Shipborne fighter (SF) Ⅰ | Execute command | |
| SF Ⅱ | Execute command | |
| Influencer ( | GBMWS | Strike the target |
| AAMWS Ⅰ | Strike the target | |
| AAMWS Ⅱ | Strike the target | |
| SAMWS | Strike the target |
| 1 | LI L Y, FAN C L, XING Q H, et al Optimal index shooting policy for layered missile defense system. Journal of Systems Engineering and Electronics, 2020, 31 (1): 118- 129. |
| 2 |
ENDER T, LEURCK R, WEAVER B, et al Systems-of-systems analysis of ballistic missile defense architecture effectiveness through surrogate modeling and simulation. IEEE System Journal, 2010, 4 (2): 156- 166.
doi: 10.1109/JSYST.2010.2045541 |
| 3 |
LIU X K, LI R, ZHAO C L, et al Robust signal recognition algorithm based on machine learning in heterogeneous networks. Journal of Systems Engineering and Electronics, 2016, 27 (2): 333- 342.
doi: 10.1109/JSEE.2016.00034 |
| 4 |
LI J C, GE B F, ZHAO D L, et al Meta-path-based weapon-target recommendation in heterogeneous combat network. IEEE System Journal, 2019, 13 (4): 4433- 4441.
doi: 10.1109/JSYST.2018.2890090 |
| 5 |
LI J C, ZHAO D L, GE B F Disintegration of operational capability of heterogeneous combat networks under incomplete information. IEEE Trans. on Systems, Man and Cybernetics, 2020, 50 (12): 5172- 5179.
doi: 10.1109/TSMC.2018.2867532 |
| 6 | GUO X C, LIU X C, CEHN G M, et al. Missile weapon system-of-systems optimization method based on information entropy. Proc. of the International Conference on Computer, Information and Telecommunication Systems, 2016. DOI: 10.1109/CITS.2016.7546453. |
| 7 | GARRETT R K, ANDERSON S, BARON N T, et al Managing the interstitials, a system of systems framework suited for the ballistic missile defense system. Journal of Systems Science and Systems Engineering, 2011, 14 (1): 87- 109. |
| 8 | WANG C G, ZHOU X D, LIU Z Y Effectiveness evaluation of a portable anti-aircraft missile’s training system based on simulation experiment. Proc. of the International Conference on Modelling and Simulation, 2009, 21- 22. |
| 9 | ALBERTS D S, GARTSKA J J, STEIN F. Network-centric warfare: developing and leveraging information superiority. Washington: Command and Control Research Program Press, 2000. |
| 10 | FRIEDMAN N. Network-centric warfare. Annapolis: Naval Institute Press, 2009. |
| 11 | DAVIS P K. Analytic architecture for capabilities-based planning, mission-system analysis, and transformation. Santa Monica: Rand, 2002. |
| 12 |
XING Q H, GAO J L A super-network equilibrium optimization method for operation architecture with fuzzy demands. Journal of Systems Engineering and Electronics, 2020, 31 (5): 969- 982.
doi: 10.23919/JSEE.2020.000072 |
| 13 |
CHEN Z R, ZHANG B Y, ZHANG Y J, et al Dissipative fuzzy filtering for nonlinear networked systems with limited communication links. IEEE Trans. on Systems, Man and Cybernetics, 2020, 50 (3): 962- 971.
doi: 10.1109/TSMC.2017.2770161 |
| 14 |
BOORSTYN R, FRANK H Large-scale network topological optimization. IEEE Trans. on Communications, 1977, 25 (1): 29- 47.
doi: 10.1109/TCOM.1977.1093708 |
| 15 |
KATO N, FADLULLAH Z M, TANG F X, et al Optimizing space-air-ground integrated networks by artificial intelligence. IEEE Wireless Communications, 2019, 26 (4): 140- 147.
doi: 10.1109/MWC.2018.1800365 |
| 16 | GASMI M, MOSBAHI O, KHALGUI M, et al Performance optimization of reconfigurable real-time wireless sensor networks. IEEE Trans. on Systems, Man and Cybernetics, 2018, 50 (7): 2623- 2637. |
| 17 | MASAZADE E, RAJAGOPALAN R, VARSHNEY P K, et al A multiobjective optimization approach to obtain decision thresholds for distributed detection in wireless sensor networks. IEEE Trans. on Systems, Man and Cybernetics, 2009, 50 (7): 2623- 2637. |
| 18 |
LUO X Y, ZHONG W J, LI X L, et al Rigid graph-based three-dimension localization algorithm for wireless sensor networks. Journal of Systems Engineering and Electronics, 2018, 29 (5): 927- 936.
doi: 10.21629/JSEE.2018.05.05 |
| 19 | SALEMA M I, BARBOSA-POVOA A P, NOVAIS A Q An optimization model for the design of a capacitated multi-product reverse logistics network with uncertainty. European Journal of Operational Research, 2007, 179 (3): 1063- 1077. |
| 20 |
SAAD A S, KHAN S A, MAHMOOD A A multi-objective evolutionary artificial bee colony algorithm for optimizing network topology design. Swarm and Evolutionary Computation, 2018, 38, 187- 201.
doi: 10.1016/j.swevo.2017.07.010 |
| 21 |
KUMAR A, PATHAK R, GUPTA Y Genetic-algorithm-based reliability optimization for computer network expansion. IEEE Trans. on Reliability, 1995, 44 (1): 63- 72.
doi: 10.1109/24.376523 |
| 22 | ZHAO J H, LIU Q P, WANG L, et al Competitiveness maximization on complex networks. IEEE Trans. on Systems, Man and Cybernetics, 2016, 48 (7): 1054- 1064. |
| 23 | PIERRE S Inferring new design rules by machine learning: a case study of topological optimization. IEEE Trans. on Reliability, 1998, 28 (5): 575- 585. |
| 24 | LYER S, KILLINGBACK T, SUNDARAM B, et al Attack robustness and centrality of complex networks. PloS One, 2013, 8 (4): e59613. |
| 25 |
FIELDER M Algebra connectivity of graphs. Czechoslovak Mathematical Journal, 1973, 23, 298- 305.
doi: 10.21136/CMJ.1973.101168 |
| 26 |
ESTRADA E, HATANOE N, BENZI M The physics of communicability in complex networks. Physics Reports, 2012, 514, 89- 119.
doi: 10.1016/j.physrep.2012.01.006 |
| 27 | CARES J R An information age combat model. Proc. of the International Command and Control Research and Technology Symposium: the Power of Information Age Concepts and Technologies, 2004, 1- 27. |
| 28 | NEWMAN M E Assortative mixing in networks. Physical Review Letters, 2002, 89 (20): 111- 118. |
| 29 |
WATTS D J, STROGATZ S H Collective dynamics of small-world networks. Nature, 1998, 393 (6684): 440- 442.
doi: 10.1038/30918 |
| 30 |
LEE Y W, LEE T Network-based metric for measuring combat effectiveness. Defense Science Journal, 2014, 64 (2): 115- 122.
doi: 10.14429/dsj.64.5534 |
| 31 | QI Y B, LIU Z, CHE H D, et al Distributed combat system of systems network modeling. Journal of Network and Computer Applications, 2013, 8 (8): 1906- 1912. |
| 32 |
MENG J Y, TUAN P C, LIU T S Discrete Markov ballistic missile defense system modeling. European Journal of Operational Research, 2007, 178 (2): 560- 578.
doi: 10.1016/j.ejor.2005.12.043 |
| 33 | JIANG J, LI X, ZHOU Z J, et al Weapon system capability assessment under uncertainty based on the evidential reasoning approach. Expert Systems with Applications, 2011, 38 (11): 13773- 13784. |
| 34 |
YANG J B, XU D L Evidential reasoning rule for evidence combination. Artificial Intelligence, 2013, 205, 1- 29.
doi: 10.1016/j.artint.2013.09.003 |
| 35 | VIDAL T, FARGIER H. Handling contingency in temporal constraint networks: from consistency to controllabilities. Journal of Experimental & Theoretical Artificial Intelligence, 1999, 11: 23–45. |
| 36 | LOANNIS T A probabilistic approach to robust execution of temporal plans with uncertainty. Proc. of the Hellenic Conference on Artificial Intelligence, 2002, 97- 108. |
| 37 |
CAHN E P, YANG Y Y Shortest path tree computation in dynamic graphs. IEEE Trans. on Computers, 2009, 58 (4): 541- 557.
doi: 10.1109/TC.2008.198 |
| 38 | DING J Y, ZHAO Q S, LI J C, et al Temporal constraint modeling and conflict resolving based on the combat process of air and missile defense system. Proc. of the IEEE International Conference on Systems, Man and Cybernetics, 2019, 2684- 2689. |
| 39 | DING J Y. Hypernetwork-based modeling, analysis and applied research of air and missile defense system. Changsha: National University of Defense Technology, 2019. |
| 40 |
SILVANDER J, ANGELIN L Introducing intents to the OODA-loop. Procedia Computer Science, 2019, 159, 878- 883.
doi: 10.1016/j.procs.2019.09.247 |
| 41 | DECHTER R, MEIRI I, PERRL J Temporal constraint networks. Artificial Intelligence, 1991, 28 (1/3): 61- 95. |
| 42 | CHERKASSKY B V, GOLDERG A V Negative-cycle detection algorithms. Proc. of the European Symposium on Algorithms, 1999, 277- 311. |
| 43 |
DEB K, PRATAP A, AGARWAL P, et al A fast and elitist multiobjective genetic algorithm: NSGA-II. IEEE Trans. on Evolutionary Computation, 2002, 6 (2): 182- 197.
doi: 10.1109/4235.996017 |
| 44 | WANG C Q, ZHANG X X, ZHAO Q S, et al Operation loop-based optimization model for resource allocation to military countermeasures versus probabilistic threat. Applied Science, 2018, 8 (2): 4568- 4573. |
| 45 | SEADA H, ABOUHAWWASH M, EDB K Towards a better balance of diversity and convergence in NSGA-III: first results. Proc. of the International Conference on Evolutionary Multi-Criterion Optimization, 2017, 545- 559. |
| 46 | ZITZLER E, LAUMANNS M, THIELE L SPEA2: improving the strength Pareto evolutionary algorithm for multiobjective optimization. Proc. of the Evolutionary Methods for Design, Optimization and Control with Applications to Industrial Problems, 2001, 19- 21. |
| 47 | YOON K, HWANG C. Multiple attribute decision making methods and applications, a state-of-the-art survey. Berlin: Springer Verlag, 1981. |
| 48 |
GANDHI M, MURUGANANTHAM A Potential influencers identification using multi-criteria decision making (MCDM) methods. Procedia Computer Science, 2015, 57, 1179- 1188.
doi: 10.1016/j.procs.2015.07.411 |
| No related articles found! |
| 阅读次数 | ||||||
|
全文 |
|
|||||
|
摘要 |
|
|||||